Cybercriminal Accused Of Millions In Office365 Executive Account Theft
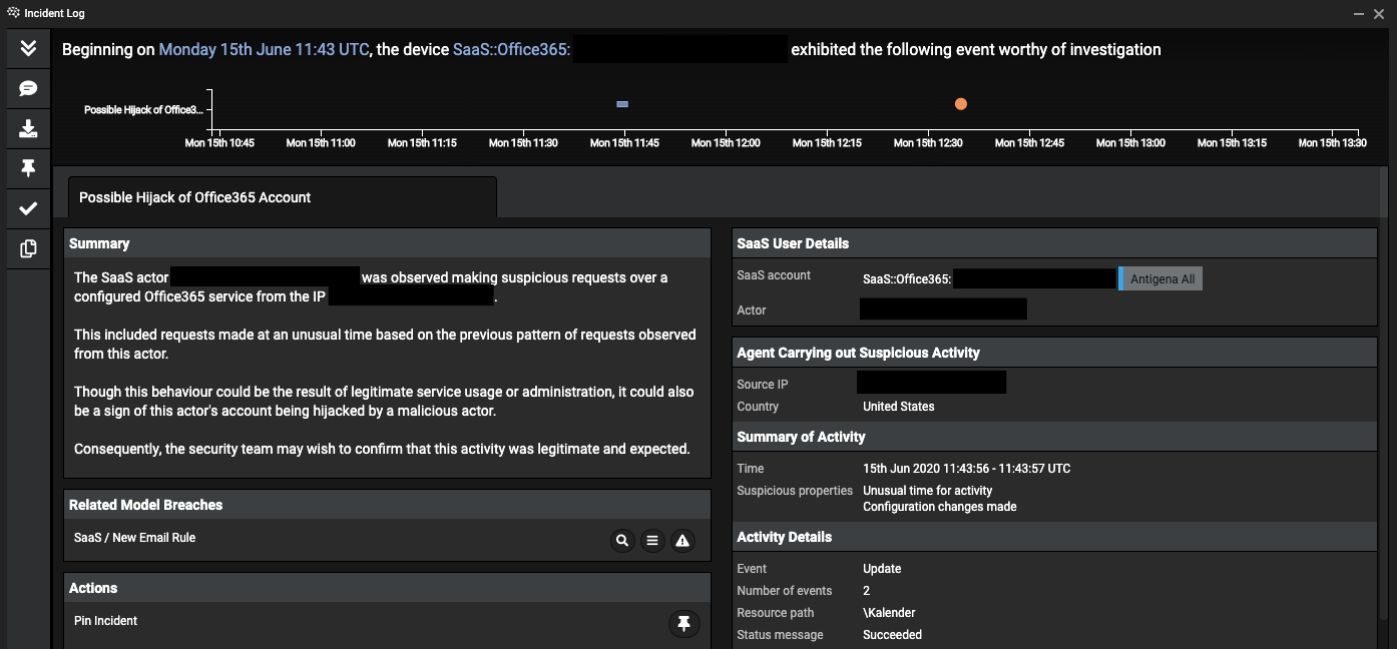
Table of Contents
The Scale of the Office365 Executive Account Breach
This recent data breach involving Office365 executive accounts resulted in substantial financial losses and a significant compromise of sensitive data. The scale of the incident is alarming, demonstrating the potential for devastating consequences when high-value accounts are targeted.
- Financial Losses: Estimates suggest the cybercriminal gained access to millions of dollars through fraudulent transactions and the exploitation of financial systems accessible through the compromised accounts. The precise figure remains under investigation, but the potential impact on the victim company is severe.
- Compromised Accounts: While the exact number remains undisclosed for security reasons, multiple executive accounts were compromised, giving the attacker access to a wide range of sensitive information. This highlights the critical need for strong access control and layered security measures.
- Data Breached: The stolen credentials granted access to a wealth of sensitive data, including financial records, strategic plans, intellectual property, and confidential communications. The exposure of this information poses a significant threat to the company's competitive advantage and operational integrity.
- Reputational Damage: The impact on the affected company's reputation is substantial. A data breach of this nature erodes trust with clients, partners, and investors. It can also lead to a negative impact on stock value and overall market confidence.
Methods Used by the Cybercriminal
The cybercriminal employed a sophisticated blend of techniques to breach the Office365 executive accounts, showcasing the evolving nature of cyber threats. Understanding these methods is crucial for effective prevention.
- Spear Phishing: The attacker likely utilized spear phishing, a highly targeted form of phishing attack that uses personalized emails to deceive executives into revealing their credentials. These emails often mimic legitimate communications from trusted sources, making them difficult to identify as malicious.
- Exploiting Vulnerabilities: While details remain under investigation, the possibility exists that the attacker exploited known or unknown vulnerabilities in the Office365 platform itself or within the company's internal systems. Regular security updates and patching are vital in mitigating these risks.
- Malware Deployment: Malware, such as keyloggers or remote access Trojans (RATs), might have been deployed to capture credentials and maintain persistent access to the compromised accounts. This underscores the importance of robust endpoint protection solutions.
- MFA Bypass: Circumventing multi-factor authentication (MFA) is a common tactic employed by sophisticated attackers. The methods used in this instance remain unclear, but it highlights the importance of strong MFA implementation and regular security assessments.
- Insider Threat (Potential): While not confirmed, the possibility of an insider threat cannot be entirely ruled out. An insider with privileged access could have facilitated the attacker's access, making thorough background checks and employee security awareness training paramount.
Legal Ramifications and Investigation
The legal consequences of this Office365 executive account theft are significant, impacting both the cybercriminal and the affected company.
- Law Enforcement Involvement: Federal agencies like the FBI, along with local law enforcement, are likely involved in the investigation, tracing the attacker's activities and gathering evidence for prosecution. International cooperation might also be necessary depending on the attacker's location.
- Charges Against the Cybercriminal: The cybercriminal faces potential charges ranging from wire fraud and identity theft to violations of federal computer crime laws, potentially resulting in lengthy prison sentences and substantial fines.
- Legal Ramifications for the Affected Company: The company faces potential legal repercussions, including regulatory fines for data breach notification failures, class-action lawsuits from affected individuals, and damage to its reputation.
- Civil Lawsuits: Victims of the breach, including employees, customers, and investors, could file civil lawsuits against the company for negligence in protecting their data, seeking compensation for damages.
Best Practices to Prevent Office365 Executive Account Theft
Protecting against Office365 executive account theft requires a multi-layered approach to cybersecurity. The following best practices are crucial:
- Strong Passwords and Password Management: Implementing strong, unique passwords for all accounts and utilizing a password manager to securely store and manage them is fundamental. Encouraging password changes on a regular basis is also vital.
- Mandatory Multi-Factor Authentication (MFA): Enforcing MFA for all Office365 accounts, especially executive accounts, is paramount. MFA adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access even if they obtain passwords.
- Regular Security Awareness Training: Providing employees, especially executives, with regular security awareness training is crucial to educate them about phishing techniques, social engineering tactics, and the importance of secure online practices. This training should cover recognizing and reporting suspicious emails and links.
- Advanced Threat Detection and Response: Implementing advanced threat detection systems that can identify and respond to malicious activities in real-time is crucial. These systems can detect anomalies and suspicious behavior, allowing for swift intervention and mitigation of potential threats.
- Comprehensive Incident Response Plan: Developing a comprehensive incident response plan that outlines procedures for handling security incidents, including data breaches, is essential. This plan should include steps for containment, eradication, recovery, and post-incident activity.
- Regular Security Audits and Penetration Testing: Regular security audits and penetration testing are necessary to identify vulnerabilities in the organization's security posture and address them proactively before attackers can exploit them.
Conclusion
The case of the cybercriminal accused of millions in Office365 executive account theft serves as a stark reminder of the ever-evolving landscape of cyber threats. The scale of the breach and the sophistication of the methods used highlight the urgent need for robust cybersecurity measures, specifically targeting the protection of high-value executive accounts. The financial, reputational, and legal implications are severe.
Don't become the next victim of Office365 executive account theft. Implement strong security practices today. Contact a cybersecurity expert to assess your vulnerability and develop a comprehensive security plan to protect your organization from similar attacks. Learn more about securing your Office365 environment and protecting your executive accounts. Proactive security measures are the best defense against this increasingly prevalent threat.

Featured Posts
-
 The State Of Affairs Federal Workers Search For Local Government Positions
Apr 28, 2025
The State Of Affairs Federal Workers Search For Local Government Positions
Apr 28, 2025 -
 The Ai Browser Battle Perplexitys Ceo On Challenging Googles Reign
Apr 28, 2025
The Ai Browser Battle Perplexitys Ceo On Challenging Googles Reign
Apr 28, 2025 -
 Cleveland Browns Draft Colorados Shedeur Sanders
Apr 28, 2025
Cleveland Browns Draft Colorados Shedeur Sanders
Apr 28, 2025 -
 Are High Gpu Prices Here To Stay
Apr 28, 2025
Are High Gpu Prices Here To Stay
Apr 28, 2025 -
 As Markets Swooned Pros Sold And Individuals Pounced A Market Analysis
Apr 28, 2025
As Markets Swooned Pros Sold And Individuals Pounced A Market Analysis
Apr 28, 2025
Latest Posts
-
 Pirates Edge Yankees In Extra Innings Thriller With Walk Off
Apr 28, 2025
Pirates Edge Yankees In Extra Innings Thriller With Walk Off
Apr 28, 2025 -
 Clutch Hits Judge And Goldschmidt Secure Yankees Series Win
Apr 28, 2025
Clutch Hits Judge And Goldschmidt Secure Yankees Series Win
Apr 28, 2025 -
 Powerhouse Performances Judge And Goldschmidt Lead Yankees To Victory
Apr 28, 2025
Powerhouse Performances Judge And Goldschmidt Lead Yankees To Victory
Apr 28, 2025 -
 Winning The Series Judge And Goldschmidts Impact On The Yankees
Apr 28, 2025
Winning The Series Judge And Goldschmidts Impact On The Yankees
Apr 28, 2025 -
 Revealed How Xs Debt Sale Reshapes Its Financial Structure
Apr 28, 2025
Revealed How Xs Debt Sale Reshapes Its Financial Structure
Apr 28, 2025
