Hegseth's Leaked Military Plans: Signal Chats Reveal Family Involvement
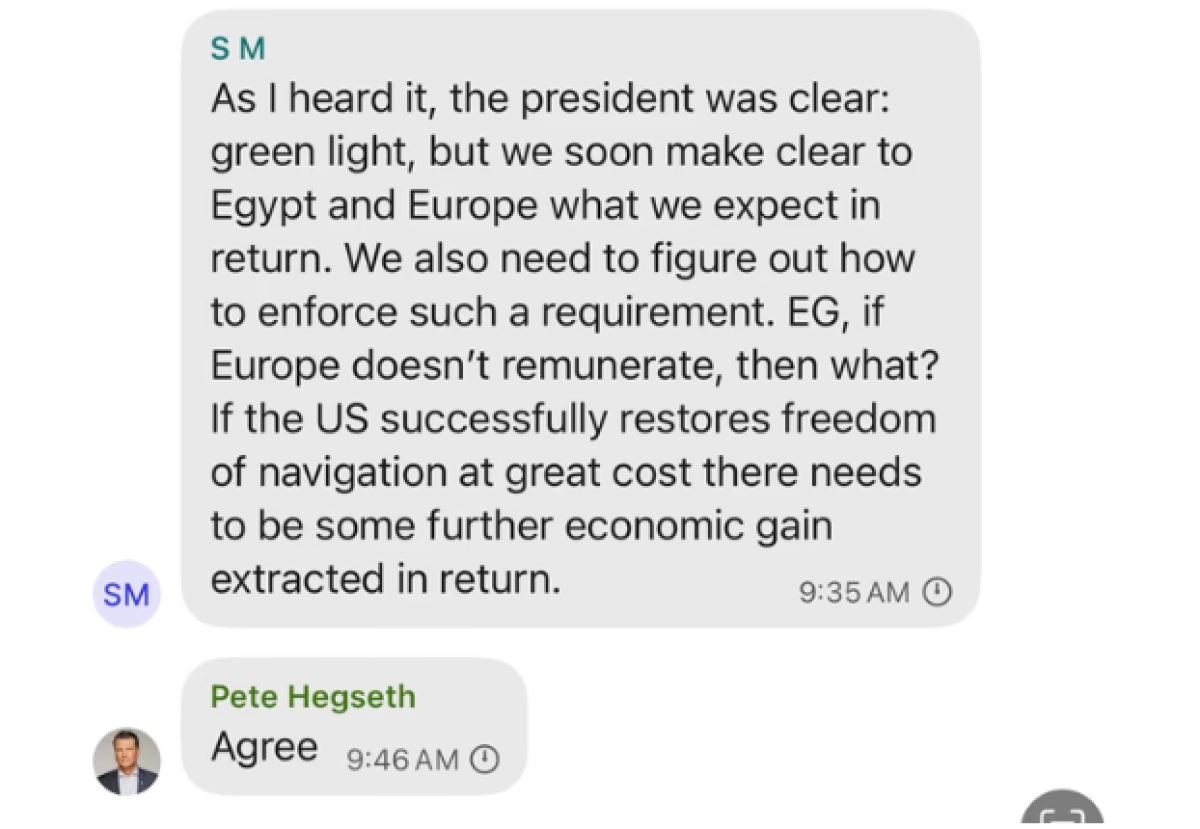
Table of Contents
The Leaked Military Plans: Content and Significance
Nature of the Leaked Information
The leaked military plans reportedly encompass a range of highly classified information pertaining to upcoming troop deployments in the Middle East. The documents, according to sources familiar with the investigation, detail:
- Specific troop movements and timelines: Precise details about the planned deployment of the 1st Armored Division to the Al-Tanf garrison.
- Operational strategies and contingency plans: Information regarding potential responses to various scenarios, including hostile actions from opposing forces.
- Sensitive intelligence gathered from HUMINT (Human Intelligence) sources: Confidential information obtained from human sources, potentially compromising ongoing operations and the safety of informants.
These leaks are classified at the Top Secret level, and their unauthorized disclosure represents a grave breach of national security. The potential damage includes compromised operations, the exposure of sensitive intelligence, and the endangerment of military personnel and informants.
The Significance of the Leak
The consequences of this leak are potentially far-reaching and catastrophic. The compromised information could:
- Cripple upcoming military operations: Enemies could anticipate and counter planned deployments, leading to significant tactical disadvantages.
- Damage international relations: Leaked plans could strain relationships with allies, leading to a loss of trust and cooperation.
- Result in loss of life: The compromised intelligence could lead to the death or capture of military personnel and civilian informants.
- Undermine public trust in the military: A significant breach of this magnitude undermines public confidence in the military's ability to safeguard national secrets.
The Role of Signal Chats in the Leak
Signal's Security Features (and vulnerabilities)
Signal is widely regarded as a secure messaging application due to its end-to-end encryption. This technology ensures that only the sender and recipient can read the messages, theoretically protecting them from interception by third parties. However, even robust encryption methods are not foolproof. Potential vulnerabilities exploited in this case might include:
- Social engineering: Hackers might have tricked a family member into revealing access codes or downloading malicious software.
- Device compromise: Malware installed on a compromised device could have logged or copied chats before encryption.
- Insider threat: A malicious actor within the family, with access to a device, could have directly leaked the information.
Evidence from Signal Chats
Evidence suggests that several incriminating messages exchanged within a family Signal group chat directly relate to the leaked military plans. Investigators have reportedly found:
- Messages referencing specific details from the leaked documents: Conversations mentioning troop deployment numbers and locations that precisely match the classified information.
- Discussions about the potential consequences of the leak: Conversations expressing awareness of the seriousness of the breach and the potential repercussions.
- Evidence of attempts to delete messages: Indicators that some messages were deleted, raising further suspicion about attempts to cover up the leak.
This evidence strongly points towards the involvement of family members in the dissemination of classified information.
The Investigation and Potential Charges
Ongoing Investigations
Multiple agencies are investigating the leak, including the FBI, military intelligence, and the Department of Justice. The investigation is focused on determining:
- The extent of the leak: The full scope of classified information that was compromised.
- The identity of all involved parties: Identifying not only Colonel Hegseth but also any family members or other individuals complicit in the leak.
- The method of the leak: Precisely how the encrypted Signal chats were accessed and the information extracted.
Charges are likely to include espionage, violation of the Espionage Act, and conspiracy to commit espionage. The severity of the charges will depend on the exact nature of the leaked information and the extent of the damage caused.
Family Involvement: Charges and Potential Sentencing
Depending on the level of their involvement, family members could face significant penalties, including:
- Espionage charges: Carrying lengthy prison sentences and substantial fines.
- Conspiracy charges: Similar penalties to espionage, based on the extent of their involvement in the conspiracy.
- Unauthorized disclosure of classified information: Significant prison time and fines, under the relevant sections of the US Code.
Precedents for similar cases, such as the Chelsea Manning and Edward Snowden cases, suggest that harsh penalties are likely if the family members are found guilty.
Conclusion
The leak of Colonel Hegseth's military plans through Signal chats, with potential family involvement, represents a severe breach of national security. The leaked information's sensitive nature and the potential consequences – compromised operations, damage to international relations, and potential loss of life – cannot be overstated. The ongoing investigation underscores the vulnerabilities within even encrypted communication platforms, highlighting the critical need for stricter security protocols and heightened awareness of the risks associated with private communication. This case of Hegseth's leaked military plans emphasizes the crucial need for rigorous vetting procedures and ongoing education regarding the handling of sensitive information. Stay informed about the unfolding investigation into Hegseth’s leaked military plans and the ramifications for national security. Continue to follow this story as developments unfold.

Featured Posts
-
 Anchor Brewing Company Closing After 127 Years The End Of An Era
Apr 22, 2025
Anchor Brewing Company Closing After 127 Years The End Of An Era
Apr 22, 2025 -
 May Hearing Could Finalize 500 Million Bread Price Fixing Settlement In Canada
Apr 22, 2025
May Hearing Could Finalize 500 Million Bread Price Fixing Settlement In Canada
Apr 22, 2025 -
 Saudi Aramco Invests In Electric Vehicle Technology With Byd Partnership
Apr 22, 2025
Saudi Aramco Invests In Electric Vehicle Technology With Byd Partnership
Apr 22, 2025 -
 Conclave 2023 Assessing Pope Francis Enduring Impact
Apr 22, 2025
Conclave 2023 Assessing Pope Francis Enduring Impact
Apr 22, 2025 -
 Is Betting On Wildfires A Sign Of The Times The Los Angeles Case
Apr 22, 2025
Is Betting On Wildfires A Sign Of The Times The Los Angeles Case
Apr 22, 2025
