Massive Office365 Data Breach Leads To Millions In Losses
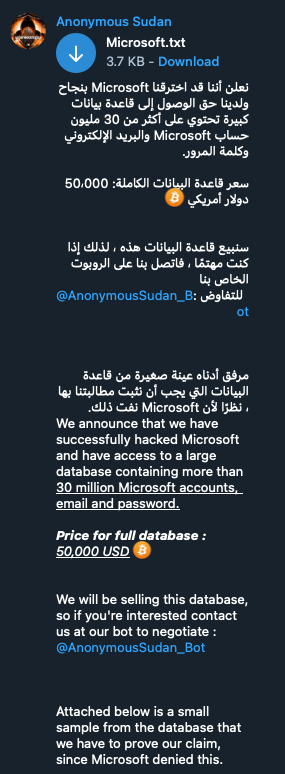
Table of Contents
Causes of Massive Office365 Data Breaches
Understanding the root causes of Office365 data breaches is the first step towards effective prevention. Several factors contribute to these devastating security incidents:
Phishing and Social Engineering Attacks
Phishing remains a leading cause of Office365 data breaches. Sophisticated phishing emails, often mimicking legitimate communications from trusted sources, trick unsuspecting employees into revealing their credentials or downloading malicious software.
- Examples: Emails claiming to be from Microsoft, requesting password resets, or containing links to fake login pages.
- Statistics: Reports show a concerningly high success rate for phishing attacks, with a significant percentage of employees falling victim to these scams. Human error remains a major vulnerability.
- Impact: Successful phishing attacks grant hackers access to sensitive company data, emails, and applications, leading to data theft, financial fraud, and reputational damage.
Weak or Stolen Credentials
Weak passwords and the practice of password reuse are significant security vulnerabilities. Hackers utilize readily available tools and techniques like credential stuffing to gain access to accounts.
- Importance of Strong Passwords and MFA: Implementing strong, unique passwords for each account and enforcing multi-factor authentication (MFA) significantly reduces the risk of unauthorized access.
- Statistics: A substantial number of data breaches are directly attributed to weak or compromised credentials.
- Recommendations for Password Management: Using a password manager to generate and securely store complex passwords is highly recommended.
Exploiting Software Vulnerabilities
Hackers actively seek vulnerabilities in Office365 applications and the underlying operating system to gain unauthorized access. Zero-day exploits, which target previously unknown vulnerabilities, pose a particularly serious threat.
- Importance of Regular Software Updates: Promptly installing software updates patches critical security flaws and reduces the window of opportunity for hackers.
- Role of Zero-Day Exploits: These are particularly dangerous as they are often undetected by existing security software.
- Need for Proactive Vulnerability Management: Regularly scanning for vulnerabilities and implementing appropriate mitigations is critical for maintaining a strong security posture.
Insider Threats
Malicious or negligent insiders with authorized access to sensitive data present a significant risk. Accidental data leaks or deliberate malicious actions by employees can have devastating consequences.
- Examples of Insider Threats: A disgruntled employee leaking confidential data or an employee accidentally sharing sensitive information with unauthorized individuals.
- Importance of Access Control and Data Loss Prevention (DLP) Measures: Implementing robust access control mechanisms and DLP measures helps to mitigate the risks posed by insider threats.
Impact of Office365 Data Breaches on Businesses
The consequences of an Office365 data breach extend far beyond the initial compromise, impacting an organization's bottom line and reputation significantly.
Financial Losses
Data breaches translate into substantial financial losses for businesses.
- Examples of Companies Affected: Numerous high-profile companies have suffered significant financial losses due to data breaches, including legal fees, regulatory fines, and the cost of recovery efforts.
- Cost of Data Recovery: Restoring compromised data and systems can be incredibly expensive.
- Cost of Notification and Remediation Efforts: Notifying affected individuals and implementing remediation strategies also add significant costs.
Reputational Damage
A data breach can severely damage a company's reputation and erode customer trust, leading to long-term negative consequences.
- Impact on Customer Loyalty: Customers may lose trust and move to competitors.
- Potential Loss of Partnerships and Investment: Damaged reputation can impact business relationships and investment prospects.
Legal and Regulatory Compliance Issues
Organizations failing to comply with data protection regulations (GDPR, CCPA, etc.) face significant legal repercussions and hefty fines.
- Examples of Hefty Fines: Regulatory bodies worldwide have imposed substantial fines on organizations for data breach failures.
- Importance of Data Breach Notification Laws: Organizations must comply with legal requirements regarding data breach notification.
Protecting Your Organization from Office365 Data Breaches
Proactive security measures are essential to mitigate the risks associated with Office365 data breaches.
Implementing Robust Security Measures
A multi-layered approach to security is crucial.
- Enforce Strong Password Policies: Implement strong password policies, including password complexity requirements and regular password changes.
- Implement Multi-Factor Authentication (MFA): MFA adds an extra layer of security, making it significantly harder for attackers to gain access.
- Regularly Update Software: Keep all software, including Office365 applications and operating systems, updated with the latest security patches.
- Use Anti-Virus and Anti-Malware Software: Employ robust anti-virus and anti-malware solutions to detect and prevent malicious software.
- Conduct Regular Security Awareness Training for Employees: Educate employees about phishing scams, social engineering tactics, and safe computing practices.
- Leverage Office365's Built-in Security Features: Utilize Office365's advanced security features, such as Advanced Threat Protection (ATP).
Data Loss Prevention (DLP)
DLP strategies and tools are crucial for preventing sensitive data from leaving the organization's control.
- Examples of DLP Tools and Strategies: Implementing data classification, access control policies, and monitoring tools.
- Role of Data Classification and Access Control: Properly classifying data and restricting access to authorized personnel.
Incident Response Planning
Having a well-defined incident response plan is critical for minimizing the impact of a data breach.
- Key Steps in an Effective Incident Response Plan: Establish clear procedures for identifying, containing, and remediating a security incident.
- Importance of Regular Testing and Updates: Regularly test and update the incident response plan to ensure its effectiveness.
Conclusion
Office365 data breaches pose a significant threat to businesses, leading to substantial financial losses and reputational damage. The causes are multifaceted, ranging from phishing attacks and weak credentials to insider threats and software vulnerabilities. Proactive security measures, including robust password policies, MFA, regular software updates, employee training, and comprehensive incident response planning, are crucial for mitigating these risks. Don't wait for a devastating Office365 data breach to strike. Assess your current security posture today and invest in the necessary solutions to protect your organization from this growing threat. Strengthen your defenses and safeguard your valuable data. Learn more about enhancing your Office365 security and explore resources for robust data protection strategies.

Featured Posts
-
 Ariana Grandes New Hair And Tattoos A Professionals Perspective
Apr 27, 2025
Ariana Grandes New Hair And Tattoos A Professionals Perspective
Apr 27, 2025 -
 Fifth Champions League Place The Premier Leagues Likely Outcome
Apr 27, 2025
Fifth Champions League Place The Premier Leagues Likely Outcome
Apr 27, 2025 -
 Crumbach Steps Down Assessing The Future Of The Spd Led Coalition In Germany
Apr 27, 2025
Crumbach Steps Down Assessing The Future Of The Spd Led Coalition In Germany
Apr 27, 2025 -
 Major Canadian Project Faces Setbacks Dows Construction Delay Explained
Apr 27, 2025
Major Canadian Project Faces Setbacks Dows Construction Delay Explained
Apr 27, 2025 -
 Binoche Chosen As President Of The Cannes Film Festival Jury
Apr 27, 2025
Binoche Chosen As President Of The Cannes Film Festival Jury
Apr 27, 2025
