Millions Stolen Via Executive Office365 Account Compromise
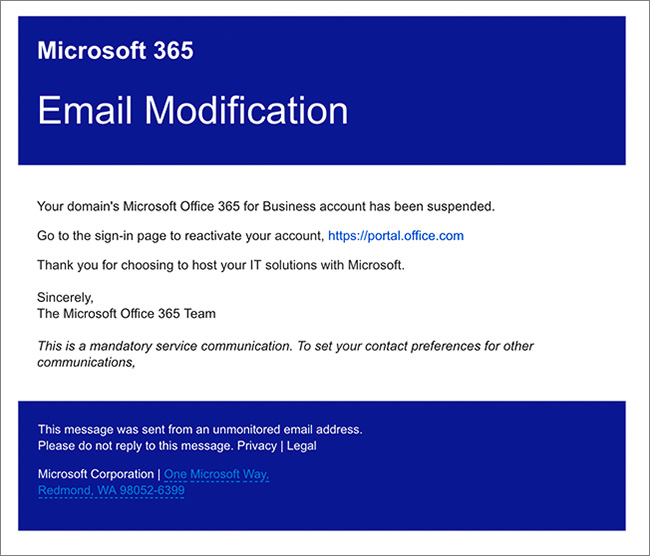
Table of Contents
The Methods Behind Executive Office 365 Account Compromises
Cybercriminals are constantly evolving their tactics, and executive accounts are often the key to unlocking a company's most sensitive data and financial resources. Several methods are employed to achieve an Executive Office 365 account compromise.
Phishing and Spear Phishing Attacks
Phishing remains a highly effective attack vector. Spear phishing, a more targeted approach, focuses specifically on executives, using personalized information to increase the likelihood of success.
- Examples of Sophisticated Phishing Emails: Emails mimicking legitimate communications from trusted sources (e.g., banks, payment processors, internal colleagues) are common. Subject lines often create a sense of urgency or importance (e.g., "Urgent: Invoice Payment Required," "Security Alert: Account Suspicious Activity").
- Techniques Used to Bypass Security Measures: Attackers utilize techniques such as using shortened URLs to mask malicious links and embedding malicious code within seemingly harmless documents. They may also exploit social engineering tactics, leveraging trust and relationships to manipulate recipients into clicking malicious links or downloading infected attachments.
- The Human Element's Role: Ultimately, the success of these attacks often hinges on human error. A single click on a malicious link can grant attackers access to an entire organization's data.
Credential Stuffing and Brute-Force Attacks
These automated attacks exploit weak passwords and stolen credentials. Credential stuffing uses known username and password combinations from previous data breaches to attempt logins, while brute-force attacks systematically try various password combinations until a match is found.
- Password Management Best Practices and the Importance of Multi-Factor Authentication (MFA): Implementing strong, unique passwords for each account is crucial. Password managers can help streamline this process, while MFA adds an extra layer of security, requiring multiple forms of authentication (e.g., password, one-time code, biometric scan) before granting access.
- Tools and Techniques Used by Attackers: Attackers utilize specialized software and scripts to automate credential stuffing and brute-force attacks, making them highly efficient at compromising accounts with weak passwords.
Exploiting Software Vulnerabilities
Outdated software and unpatched vulnerabilities create entry points for attackers. Exploiting these flaws allows them to gain unauthorized access to systems and data.
- Importance of Regular Software Updates and Security Patches: Keeping all software, including operating systems, applications, and Office 365 itself, up-to-date with the latest security patches is paramount. Regular updates often include critical security fixes that address known vulnerabilities.
- Specific Vulnerabilities that Have Been Exploited in the Past: Numerous vulnerabilities have been discovered and exploited in various software applications, highlighting the constant need for vigilance and prompt patching.
Insider Threats
Malicious or negligent insiders pose a significant risk. Employees with access to sensitive data could inadvertently or deliberately compromise the security of executive accounts.
- Preventative Measures: Implementing strict access control policies, regularly monitoring employee activity (with appropriate privacy considerations), and establishing robust security policies are vital to mitigating insider threats. Thorough background checks and security awareness training can also help minimize risk.
The Devastating Consequences of an Executive Office 365 Account Compromise
The consequences of a successful Executive Office 365 account compromise can be far-reaching and devastating.
Financial Losses
The financial impact can be substantial, encompassing:
- Examples of Real-World Cases and Associated Costs: Numerous cases demonstrate the significant financial losses resulting from data breaches and ransomware attacks facilitated by compromised executive accounts, leading to millions of dollars in losses.
- Fraudulent Transactions, Data Breaches, and Ransom Demands: Attackers may use compromised accounts to initiate fraudulent transactions, steal sensitive data for resale or blackmail, or demand ransom payments to restore access to systems.
Reputational Damage
A data breach can severely damage a company's reputation and erode customer trust.
- Long-Term Effects on Customer Relationships and Investor Confidence: The negative publicity associated with a breach can lead to a loss of customers, diminished investor confidence, and difficulties attracting future business.
Legal and Regulatory Penalties
Non-compliance with data protection regulations can result in substantial fines and legal repercussions.
- Relevant Regulations Like GDPR and CCPA: Organizations must adhere to regulations like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), facing significant penalties for data breaches and non-compliance.
Protecting Your Executive Office 365 Accounts: Proactive Security Measures
Protecting executive Office 365 accounts requires a multi-layered approach combining technological solutions and robust security policies.
Implementing Multi-Factor Authentication (MFA)
MFA is no longer optional; it's essential.
- Different MFA Methods and Their Strengths: Implement a range of MFA methods, including time-based one-time passwords (TOTP), authenticator apps, security keys, and biometric authentication, to provide robust protection against unauthorized access.
Strong Password Policies and Password Management
Enforce strong password policies and encourage the use of password managers.
- Recommendations for Password Complexity and Rotation: Require complex passwords with a minimum length, a mix of uppercase and lowercase letters, numbers, and symbols, and implement regular password rotation policies.
Regular Security Awareness Training
Educate employees on recognizing and avoiding phishing attempts.
- Methods for Effective Security Awareness Programs: Conduct regular security awareness training, using simulated phishing campaigns and interactive modules to teach employees how to identify and report suspicious emails and activities.
Advanced Threat Protection (ATP)
Leverage Office 365's built-in ATP features.
- Specific Features Like Anti-Phishing, Anti-Malware, and Secure Email Gateways: ATP provides advanced threat protection capabilities, including anti-phishing and anti-malware protection, secure email gateways, and real-time threat detection.
Regular Security Audits and Penetration Testing
Proactively identify and address vulnerabilities.
- Benefits of Regular Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify weaknesses in your security posture and proactively address potential vulnerabilities before attackers can exploit them.
Conclusion
An Executive Office 365 account compromise represents a significant threat to any organization, leading to devastating financial and reputational consequences. Implementing robust security measures, including MFA, strong password policies, regular security awareness training, ATP, and proactive security assessments, is crucial for protecting your executive accounts and preventing these potentially catastrophic events. Don't wait until it's too late. Take action today to safeguard your organization. Contact us for a free consultation on strengthening your Office 365 security and preventing executive account compromises. Learn more about securing your organization by exploring our resources on Office 365 security best practices today.

Featured Posts
-
 1050 V Mware Price Hike At And Ts Concerns Over Broadcoms Acquisition
Apr 27, 2025
1050 V Mware Price Hike At And Ts Concerns Over Broadcoms Acquisition
Apr 27, 2025 -
 Cerundolo Avanza A Cuartos De Final En Indian Wells Ausencias De Fritz Y Gauff Marcan El Torneo
Apr 27, 2025
Cerundolo Avanza A Cuartos De Final En Indian Wells Ausencias De Fritz Y Gauff Marcan El Torneo
Apr 27, 2025 -
 Novak Djokovics Early Exit From Monte Carlo Masters 2025
Apr 27, 2025
Novak Djokovics Early Exit From Monte Carlo Masters 2025
Apr 27, 2025 -
 German Coalition Stability Questioned After Crumbachs Resignation From Bsw
Apr 27, 2025
German Coalition Stability Questioned After Crumbachs Resignation From Bsw
Apr 27, 2025 -
 Real Time Analysis How A Canadian Travel Boycott Affects The American Economy
Apr 27, 2025
Real Time Analysis How A Canadian Travel Boycott Affects The American Economy
Apr 27, 2025
