Millions In Losses: FBI Probes Office365 Executive Email Account Breaches

Table of Contents
The FBI is investigating significant financial losses resulting from Office365 executive email account breaches. This isn't just another cybersecurity story; it's a wake-up call highlighting the vulnerability of even the most sophisticated businesses to highly targeted attacks. This article explores the methods used, the vulnerabilities exploited, and the crucial steps businesses can take to protect themselves.
The Scale of the Problem: Financial Losses from Office365 Breaches
The financial fallout from Office365 executive email account breaches is immense. While precise figures remain under wraps due to ongoing investigations, the losses are measured in millions of dollars for many affected companies. The average cost per breach, according to recent industry reports, can easily exceed $1 million, factoring in various factors.
-
Examples of financial losses:
- Ransomware payments: Criminals often encrypt critical data and demand significant ransoms for its release.
- Lost revenue due to business disruption: Breaches can cripple operations, leading to lost sales and project delays.
- Legal fees and regulatory fines: Companies face substantial legal costs to address the breach, and potential fines for non-compliance with regulations like GDPR.
- Reputational damage: The fallout from a data breach can severely damage a company's reputation and erode investor confidence, impacting its stock price and long-term prospects.
-
Statistics: Although precise figures related to this specific FBI investigation are unavailable publicly, studies show a significant increase in Office365 breaches targeting executives specifically. These attacks often leverage the executive's influence within the company to cause maximum damage.
FBI Investigation: Tactics Used by Cybercriminals
The FBI's investigation sheds light on the sophisticated tactics employed by cybercriminals to breach Office365 executive accounts. These aren't random attacks; they're highly targeted and meticulously planned.
-
Phishing attacks: These remain a primary vector. Criminals craft convincing emails mimicking legitimate communications from trusted sources, often including links to malicious websites or attachments containing malware. These emails frequently leverage urgency or a sense of importance to pressure the recipient into action.
-
Credential stuffing: Criminals use lists of stolen usernames and passwords obtained from previous breaches to try and access Office365 accounts. This is particularly effective against users who reuse passwords across multiple platforms.
-
Exploiting vulnerabilities in Office365: While Microsoft regularly patches security vulnerabilities, attackers often exploit zero-day vulnerabilities or flaws in poorly configured systems. Outdated software and plugins represent significant weaknesses.
-
Malware and other malicious software: Once access is gained, criminals often deploy malware to steal data, install backdoors, or control the compromised account for future attacks.
Vulnerable Points in Office365 Security and Prevention Strategies
Several weaknesses in Office365 security make executive accounts particularly vulnerable. These vulnerabilities are often interconnected and can be exploited in combination.
-
Lack of multi-factor authentication (MFA): MFA adds an extra layer of security, requiring users to provide multiple forms of authentication (e.g., password, code from a mobile app, biometric scan) to access their accounts. Its absence significantly weakens security.
-
Weak or reused passwords: Using weak or easily guessable passwords and reusing passwords across different platforms makes accounts highly susceptible to credential stuffing attacks.
-
Insufficient employee security training: Employees need thorough training to recognize and avoid phishing attacks and other social engineering tactics. This training should be regularly updated to cover the latest threats.
-
Outdated security software: Keeping all security software updated and configured correctly is crucial to protect against malware and other threats.
Preventative Measures:
- Implement MFA: This is arguably the most critical step.
- Enforce strong password policies: Require complex passwords and regular password changes.
- Provide comprehensive security awareness training: Educate employees on phishing, social engineering, and other threats.
- Regularly update security software and patches: Stay up-to-date on the latest security updates from Microsoft and other vendors.
- Conduct regular security audits: Identify and address potential vulnerabilities in your Office365 setup.
The Impact on Businesses and the Importance of Proactive Security
The long-term consequences of an Office365 executive email breach can be devastating.
-
Reputational damage: A breach can severely damage a company's reputation, eroding trust among customers, partners, and investors.
-
Loss of customer trust: Customers may be hesitant to do business with a company that has suffered a data breach.
-
Legal and regulatory repercussions: Companies can face hefty fines for failing to comply with data protection regulations such as GDPR.
-
Increased insurance premiums: Cybersecurity insurance premiums are likely to increase significantly after a breach.
Proactive Security is Key: A reactive approach to cybersecurity is insufficient. Businesses must adopt a proactive strategy, regularly assessing their security posture, implementing robust security protocols, and staying ahead of evolving threats.
Conclusion
The FBI's investigation into Office365 executive email account breaches underscores the critical need for robust cybersecurity measures. The financial losses involved are substantial, and the reputational damage can be irreversible. Criminals are employing increasingly sophisticated tactics, exploiting weaknesses in security practices and vulnerabilities within Office365 itself. To avoid becoming a victim, businesses must prioritize the following:
- Conduct a thorough security audit of your Office365 environment.
- Implement multi-factor authentication (MFA) for all accounts, especially executive accounts.
- Provide regular, comprehensive security awareness training to all employees.
- Maintain updated security software and patches.
Don't wait for a breach to occur. Protect your Office 365 accounts and safeguard your business by taking immediate action. Ignoring these threats is simply not an option.

Featured Posts
-
 Closer Security Links Forged Between China And Indonesia
Apr 22, 2025
Closer Security Links Forged Between China And Indonesia
Apr 22, 2025 -
 Fp Video Interviews Economists Understanding The Bank Of Canadas Rate Pause
Apr 22, 2025
Fp Video Interviews Economists Understanding The Bank Of Canadas Rate Pause
Apr 22, 2025 -
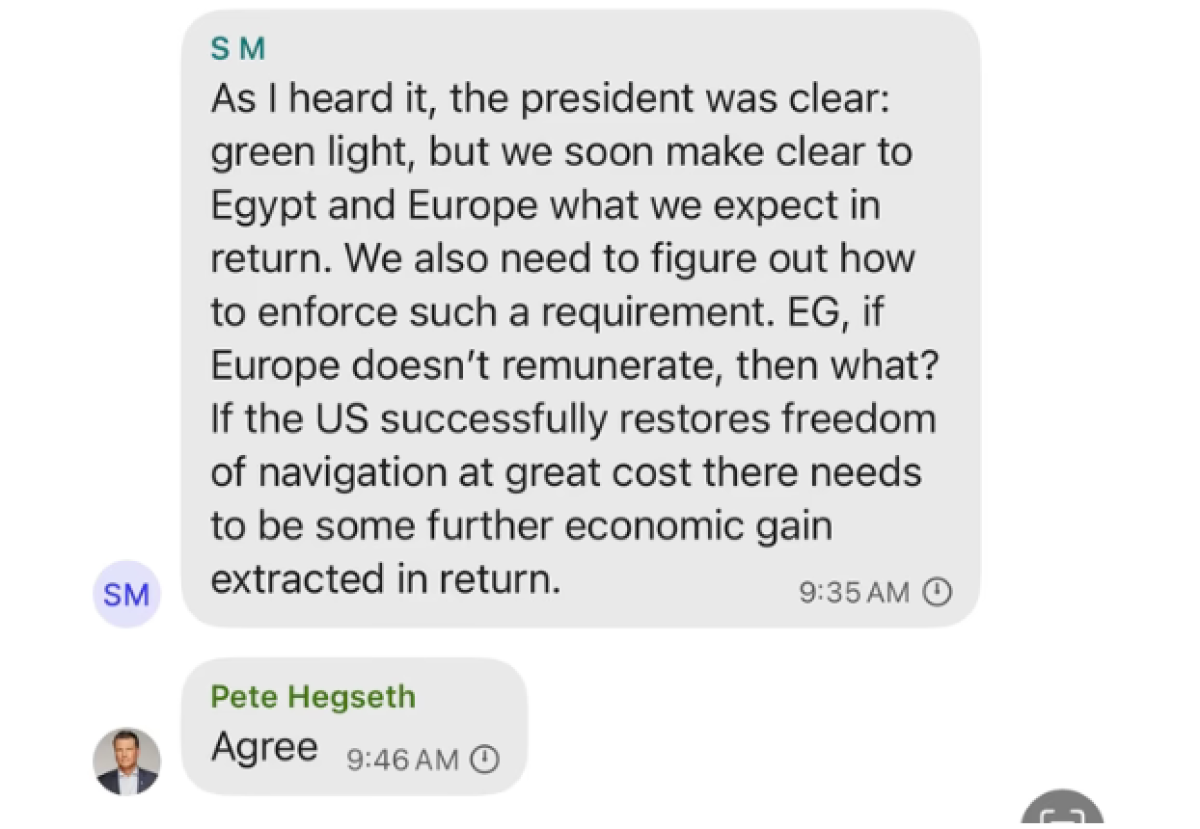 Hegseths Leaked Military Plans Signal Chats Reveal Family Involvement
Apr 22, 2025
Hegseths Leaked Military Plans Signal Chats Reveal Family Involvement
Apr 22, 2025 -
 Kyiv Faces Trumps Ukraine Peace Plan A Ticking Clock
Apr 22, 2025
Kyiv Faces Trumps Ukraine Peace Plan A Ticking Clock
Apr 22, 2025 -
 Fox News Faces Defamation Lawsuit From Trump Supporter Ray Epps Over January 6th Claims
Apr 22, 2025
Fox News Faces Defamation Lawsuit From Trump Supporter Ray Epps Over January 6th Claims
Apr 22, 2025
